Featured
Table of Contents
- – Ipsec Configuration - Win32 Apps
- – Ssl Vpns Vs. Ipsec Vpns: Vpn Protocol Differen...
- – What An Ipsec Vpn Is, And How It Works
- – Ip Security (Ipsec)
- – How Do Ipsec And Vpn Work?
- – What Is Ipsec Protocol? How Ipsec Vpns Work
- – Ipsec: A Comprehensive Guide - Techgenix
- – Data Encryption And Authentication - Ipsec
- – What Is Ipsec?
- – What Is Ipsec?
Ipsec Configuration - Win32 Apps
Cryptographic secrets are likewise disposed of. IPSec VPN, many of the best VPN companies can also utilize SSL VPN to protect your connection over the web. Depending upon the level of security required, VPN companies can carry out both or pick one over the other. SSL VPNs rely on the procedure.
Therefore, the security and applications of IPSec VPN and SSL VPN differ. With IPSec VPN, your traffic is secure as it moves to and from private networks and hosts; in a nutshell, you can safeguard your whole network.
Ssl Vpns Vs. Ipsec Vpns: Vpn Protocol Differences ...


We have all heard of SSL. SSL is what makes it possible for things like e-commerce to thrive. SSL lets us interact with websites safely, however what do we do if we require to connect to another network privately rather of a site? That's when you utilize IPSec. A great deal of new IT techs and system admins don't fully understand IPSec.
IPSec is a technique of protected, encrypted communications between a customer and a network. That interaction is sent out through public networks such as the web.
What An Ipsec Vpn Is, And How It Works
That indicates that IPSec can possibly be more protected than other methods of secure interaction. IPSec connections are still made between the customer and host through other networks, nevertheless. Those other networks are typically public networks like the internet, too. So, all interactions in between the customer and host are secured.
That's because the entire package of data is encrypted during interactions. You might think that all packages need readable headers to get to their location effectively, and you would be.
Ip Security (Ipsec)
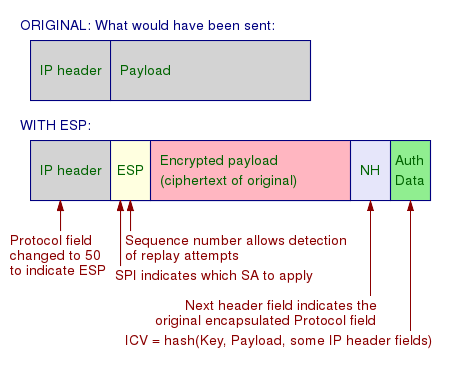
ESP includes new header information and trailers (comparable to headers however at the end of a packet) for transportation while the real header stays encrypted. Also, each package is authenticated too. The IPSec host will validate that each packet of data got was sent by the entity that the host believes sent it.
IPSec is utilized to create a protected approach of communication between a client and a host. That customer could be something like a laptop computer. Similarly, that customer might also be a personal network. The host is generally a personal network, too. We understand how IPsec works, but what is IPSec utilized for? What does that paragraph above even imply? IPSec is usually utilized for VPNs.
How Do Ipsec And Vpn Work?
Today, though, they can communicate over the open internet utilizing an IPsec connection. In numerous ways, an IPsec connection and a TLS or SSL connection are comparable. In lots of other methods, however, IPsec and TLS or SSL connections are extremely different, too.
Thus, IPsec connections begin at the fundamental connection level of the OSI design. In contrast, TLS and SSL connections start higher up the stack. Second, TLS and SSL connections depend on the application layer (HTTP) and layer 4 (TCP) to work. That suggests they are also susceptible to exploits in those layers, whereas IPsec may not be.
What Is Ipsec Protocol? How Ipsec Vpns Work
Due To The Fact That TLS and SSL connections utilize TCP, those protected connection types require to be negotiated first. When negotiated, the customer and host will concur on a file encryption secret, too. IPSec is different. Interaction is encrypted instantly. In fact, the secret key used for encryption requires to be shared in between the customer and host individually prior to any communications can be tried.
The approach used for crucial exchanges in IPsec is called IKEv1 or IKEv2. Since IPsec connections are secured right away, the whole header of the IP packet can be secured, too.
Ipsec: A Comprehensive Guide - Techgenix
Network admins need to take care to make allowances for those size differences in their network. IPSec is a technique of safe and secure, encrypted interaction between a customer and a host.
The host is generally a personal network. IPsec itself is not a protocol but rather a handful of protocols used together.
Data Encryption And Authentication - Ipsec
Virtual personal network (VPN) is a technology for establishing a personal network on a public network. It is a logical network over a public network such as the Web, enabling user information to be transmitted through a logical link. This is different from a conventional private network, where user information is sent through an end-to-end physical link.
In this phase, the interacting parties use the Web Key Exchange (IKE) protocol to establish IKE SAs for identity authentication and essential details exchange, and then establish IPsec SAs for safe and secure information transmission based on the IKE SAs. Data transmission. After IPsec SAs are established between the interacting celebrations, they can transfer data over an IPsec tunnel.
What Is Ipsec?
If the ICVs obtained at both ends are the same, the packet is not tampered with throughout transmission, and the receiver decrypts the package. IPsec file encryption and authentication process Tunnel teardown.
That is, AH guarantees that the source of IP packages is trusted and the data is not tampered with. An AH header is added to the standard IP header in each information packet.
What Is Ipsec?
An ESP header is appended to the standard IP header in each information package, and the ESP Trailer and ESP Auth data fields are added to each data packet. ESP in transport mode does not inspect the stability of IP headers. ESP can not ensure that IP headers are not tampered with.
The following compares IPsec VPN and SSL VPN: Working layers of the OSI referral design, OSI specifies a seven-layer framework for network interconnection: physical layer, data connect layer, network layer, transportation layer, session layer, discussion layer, and application layer. IPsec works at the network layer and straight runs over the Internet Protocol (IP).
Table of Contents
- – Ipsec Configuration - Win32 Apps
- – Ssl Vpns Vs. Ipsec Vpns: Vpn Protocol Differen...
- – What An Ipsec Vpn Is, And How It Works
- – Ip Security (Ipsec)
- – How Do Ipsec And Vpn Work?
- – What Is Ipsec Protocol? How Ipsec Vpns Work
- – Ipsec: A Comprehensive Guide - Techgenix
- – Data Encryption And Authentication - Ipsec
- – What Is Ipsec?
- – What Is Ipsec?
Latest Posts
Best Vpns For Freelancers And Remote Workers: Protect ...
18 Best Vpn Services To Protect Your Online Privacy + ...
16 Best Vpn For Android & Ios In 2022 [Free & Paid]
More
Latest Posts
Best Vpns For Freelancers And Remote Workers: Protect ...
18 Best Vpn Services To Protect Your Online Privacy + ...
16 Best Vpn For Android & Ios In 2022 [Free & Paid]